Not just to save your 4G data bundle, but also great to squeeze the most out of a crappy Wi-Fi hotspot when abroad (or on the ‘Wi-Fi in de Trein’ in NL). By blocking large background transfers like CrashPlan, Box and Google Drive, the limited bandwidth is all available for your foreground tasks!
-
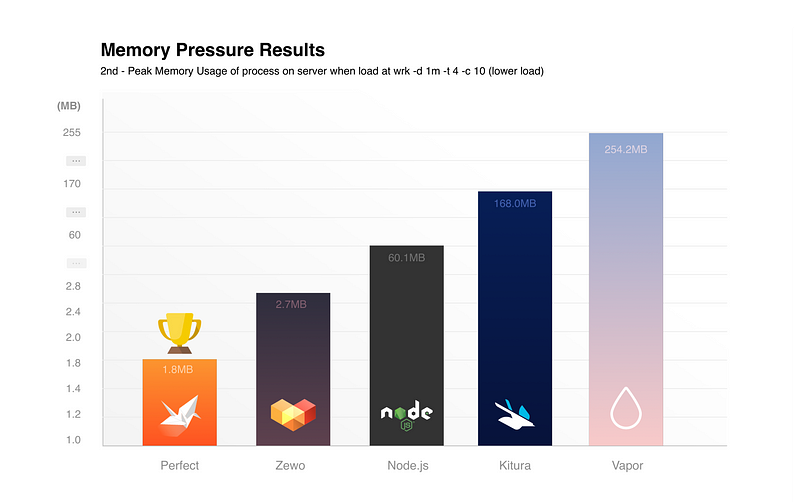
Benchmarks for the Top Server-Side Swift Frameworks vs. Node.js
Very interesting research, even if already a few months old. Interesting to see how this space will develop in 2017!
Edit Oct 7th: Checkout my Follow Up: Benchmarks for Linux (Ubuntu)
Source: Benchmarks for the Top Server-Side Swift Frameworks vs. Node.js
-
Hans Rosling | World Health Statistics expert extraordinaire
In Hans Rosling’s hands, data sings. Global trends in health and economics come to vivid life. And the big picture of global development—with some surprisingly good news—snaps into sharp focus.
Source: Hans Rosling | Speaker | TED.com
-
Great resource: OS X terminal shell commands.
Great read, should give anyone a few nifty new nuggets.
awesome-osx-command-line – Use your OS X terminal shell to do awesome things.
-
Will AI be a nice God?
This blog is a must read for anyone interested in technology and innovation.
“Creating the technology to reverse human aging, curing disease and hunger and even mortality, reprogramming the weather to protect the future of life on Earth—all suddenly possible. Also possible is the immediate end of all life on Earth. As far as we’re concerned, if an ASI comes to being, there is now an omnipotent God on Earth—and the all-important question for us is:
Will it be a nice God?”
Part 1 of 2: “The Road to Superintelligence”. Artificial Intelligence — the topic everyone in the world should be talking about.
Source: The Artificial Intelligence Revolution: Part 1 – Wait But Why
-
From mobile first to mobile native — Benedict Evans
Smart companies are starting to build solutions with a “mobile native” assumption:
This change, from building on mobile ‘first’ to really leveraging what a billion or so high-end smartphones can do in 2016, reminds me a little of the ‘Web 2.0’ products of a decade or so ago. One (and only one) way you could characterize these is that they said: ”you know, we don’t necessarily have to think about Lynx, and CGI scripts, and IE2, and dialup. We’ve evolved the web beyond the point that
tags were controversial and can make new assumptions about what will work, and that enables new ways to think about interfaces and services.”
-
Must-read for speaking in public "Doing a TED Talk: The Full Story – Wait But Why"
In August of 2015, Tim Urban, the author of Wait But Why, was invited to give a TED Talk. Here’s his full story on how to do a great talk – or wing it during a informal speech… .
Source: Doing a TED Talk: The Full Story – Wait But Why
Prep spectrum illustration -
Cleaning B&W C5 Earphones
After many months of use; the sound level of my B&W C5 in-ears was starting to degrade – to the point where even with volume control turned all the way up on my iPhone, music or conference calls became hard to hear. Clogged!
Google did not have any good results on how to fix this. Common suggestions for in-ear buds include cleaning with a cloth, a soft brush and some detergent (lukewarm soapy water, alcohol etc). This did not work for me – the fine metal mesh in the in-ear piece appeared to be stubbornly clogged.

B&W C5, showing metal screen While some users reported successfully opening the earbuds with a vice and pliers, that seemed too destructive to me.

B&W C5, taken apart Luckily, I tried the following as a last resort: carefully sticking a needle in the mesh allows to exert enough pulling force to remove the screen from the earbud.
Taking out the metal screens allows me to clean them easily, fully restoring the sound output to its original, glorious levels.
After cleaning, the mesh screen can be easily placed back in its original position. In my case, the remaining glue residu was sufficient to keep it in place, but you could carefully add a small amount of glue to be safe.
-
New Years Resolutions
“Want to make sure you nail your 2015 resolutions? Make them public, psychologists advised.” Consider this a brain dump first and a way to create some accountability to myself second. Anything else is a bonus. So here we go!
This is a work in progress. Until 31-12; I should be able to edit, right?! Any suggestions or helpful hints are welcomed. I may have to order these goals somehow at one point…and maybe do some pattern recognition to look for a deeper coherence?